SolarWinds provides network security appliances to corporations. And governments. And universities. These organizations depend on companies like SolarWinds because security is VERY hard and it helps to get outside help. You can take my word for it to a degree - I worked in IT for over three decades, and while I did not specifically work in computer/network security, I had enough exposure to it to understand what a huge, tiresome, endless, and thankless job it was. It was truly neverending. You never had enough money or resources, and you were always outnumbered by the baddies.
Now what happens when a company like SolarWinds gets hacked?
I guess the first thing to talk about would be the nature of the hack. Let's suppose an update that SolarWinds pushes out to all of their customers was compromised. Now, ALL of your customers are vulnerable to being infiltrated by the people who compromised SolarWinds.
Perhaps it was a nation-state who did it.
Perhaps Russia.
Let's take a look at who makes up SolarWinds customer list. Here's a listing from SolarWinds' web site:
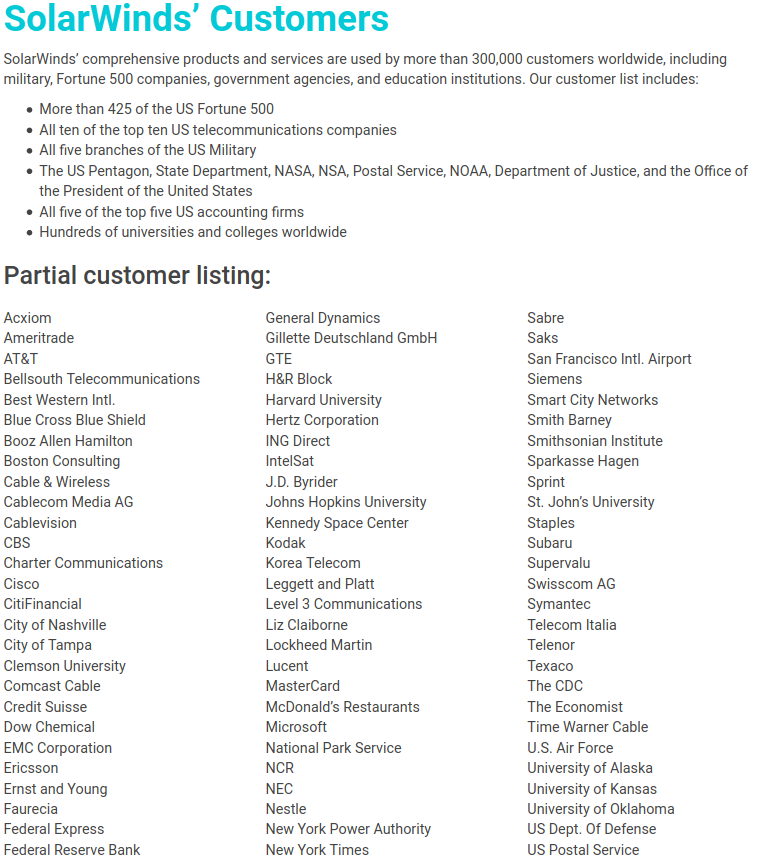
Notice any familiar names there?
I thought not.
So basically, Russian hackers, some of which are largely synonymous with the Russian government, compromised pretty much the entirety of the United States Government. And the U.S. Military. And effectively the entirety of the S&P 500.
Yeah, and our President has poo-poohed Russian election interference and sucked up to Putin for how long?
https://krebsonsecurity.com/2020/12/u-s-treasury-commerce-depts-hacked-through-solarwinds-compromise/
https://www.schneier.com/blog/archives/2020/12/another-massive-russian-hack-of-us-government-networks.html
Now what happens when a company like SolarWinds gets hacked?
I guess the first thing to talk about would be the nature of the hack. Let's suppose an update that SolarWinds pushes out to all of their customers was compromised. Now, ALL of your customers are vulnerable to being infiltrated by the people who compromised SolarWinds.
Perhaps it was a nation-state who did it.
Perhaps Russia.
Let's take a look at who makes up SolarWinds customer list. Here's a listing from SolarWinds' web site:

Notice any familiar names there?
I thought not.
So basically, Russian hackers, some of which are largely synonymous with the Russian government, compromised pretty much the entirety of the United States Government. And the U.S. Military. And effectively the entirety of the S&P 500.
Yeah, and our President has poo-poohed Russian election interference and sucked up to Putin for how long?
https://krebsonsecurity.com/2020/12/u-s-treasury-commerce-depts-hacked-through-solarwinds-compromise/
https://www.schneier.com/blog/archives/2020/12/another-massive-russian-hack-of-us-government-networks.html
no subject
Date: 2020-12-17 06:03 pm (UTC)Ah, no more taking hubs and putting them in promiscuous mode, eh? Yeah, it's been a lot of years since I had my CCNA. You're absolutely right, those old hubs are probably capped at 10 mbs and our connection at home is a fiber at 50/50. Considering we live literally on top of a mountain in the middle of a national forest, that's pretty darn spiffy!
no subject
Date: 2020-12-22 05:25 pm (UTC)no subject
Date: 2020-12-22 10:32 pm (UTC)You're right. With the hub automatically flooding everything across all ports, it would be the card in the monitoring device that would be in promiscuous. Probably just end up with a RasbPi for monitoring if I ever get around to sniffing my own traffic.
no subject
Date: 2020-12-23 08:15 pm (UTC)no subject
Date: 2020-12-23 08:52 pm (UTC)I will look in to that, thanks!