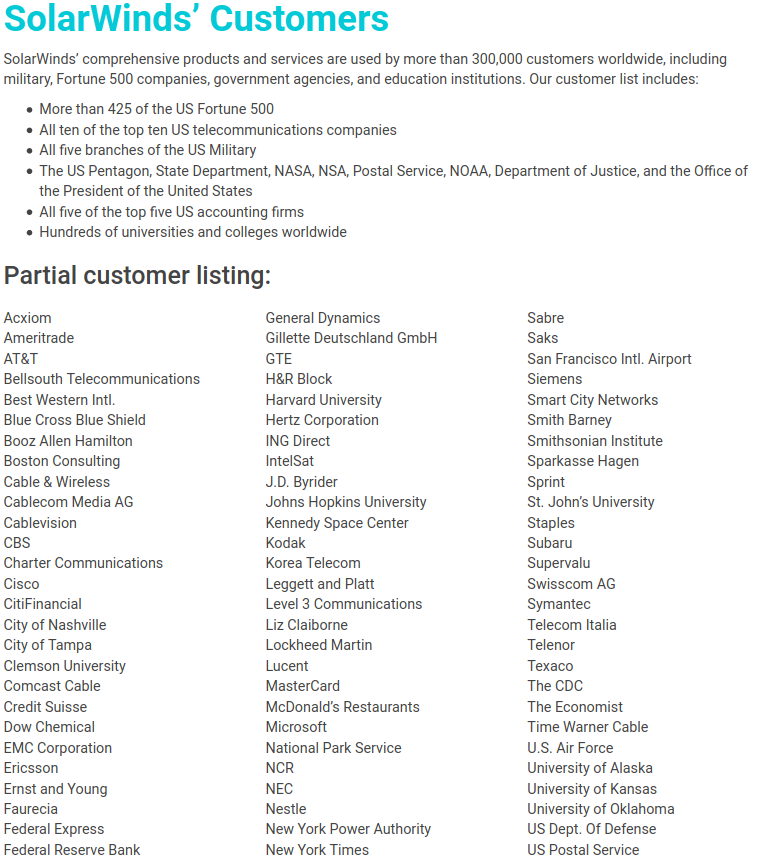
This is bad, for both Russia and the USA.
There was a successful launch Thursday from Pad 31 in Kazakstan of a Soyuz rocket carrying two Russian cosmonauts and one American astronaut to the ISS. But there was a problem on the ground.
One of the launch tower's moving platforms that is used to inspect and service the rocket was not properly secured prior to launch. The blast from the rocket passing the platform blew it down into the flame trench, causing a lot of damage to the pad, probably the tower, and presumably destroying the platform - which weighed 20 tons. Roscomos, the agency that runs the Russian space program (roughly the equivalent of NASA) claims that the damage will be repaired shortly. However, so many materials in manpower, money, and actual physical materials have been diverted to their failing war effort against Ukraine that this might not happen. One specific example of how Roscomos is being squeezed is that they used to send four crews to the ISS annually, now they're sending three.
While Russia has many launch facilities through its countries and neighbors, i.e. former USSR countries, Pad 31 is currently the only launch pad that can be used to send Soyuz and Proton rockets to the ISS. Pad 1 at the Kazakstan facility - where Uri Gregarin launched from - could be used, but it's been decommissioned and is being turned into a museum.
The Soyuz launches are used for crew/supply missions, the Proton launches are solely supply runs but also used to boost the ISS into a higher orbit. Fortunately NASA can also use SpaceX Dragons and Northrop Grumman’s Cygnusfor boost and also for supply.
This will also put some pressure on SpaceX as they've been having some problems with their super-heavy booster, trying to get it reliable enough to get people to the Moon and allegedly to Mars, not to mention their lunar lander being so far behind schedule that NASA is sending out an SOS contract for someone else to come up with another lander, otherwise SpaceX's tardiness will delay the USA going back to the Moon.
https://arstechnica.com/space/2025/11/russian-launch-pad-incident-raises-concerns-about-future-of-space-station/
There was a successful launch Thursday from Pad 31 in Kazakstan of a Soyuz rocket carrying two Russian cosmonauts and one American astronaut to the ISS. But there was a problem on the ground.
One of the launch tower's moving platforms that is used to inspect and service the rocket was not properly secured prior to launch. The blast from the rocket passing the platform blew it down into the flame trench, causing a lot of damage to the pad, probably the tower, and presumably destroying the platform - which weighed 20 tons. Roscomos, the agency that runs the Russian space program (roughly the equivalent of NASA) claims that the damage will be repaired shortly. However, so many materials in manpower, money, and actual physical materials have been diverted to their failing war effort against Ukraine that this might not happen. One specific example of how Roscomos is being squeezed is that they used to send four crews to the ISS annually, now they're sending three.
While Russia has many launch facilities through its countries and neighbors, i.e. former USSR countries, Pad 31 is currently the only launch pad that can be used to send Soyuz and Proton rockets to the ISS. Pad 1 at the Kazakstan facility - where Uri Gregarin launched from - could be used, but it's been decommissioned and is being turned into a museum.
The Soyuz launches are used for crew/supply missions, the Proton launches are solely supply runs but also used to boost the ISS into a higher orbit. Fortunately NASA can also use SpaceX Dragons and Northrop Grumman’s Cygnusfor boost and also for supply.
This will also put some pressure on SpaceX as they've been having some problems with their super-heavy booster, trying to get it reliable enough to get people to the Moon and allegedly to Mars, not to mention their lunar lander being so far behind schedule that NASA is sending out an SOS contract for someone else to come up with another lander, otherwise SpaceX's tardiness will delay the USA going back to the Moon.
https://arstechnica.com/space/2025/11/russian-launch-pad-incident-raises-concerns-about-future-of-space-station/